Table of Contents
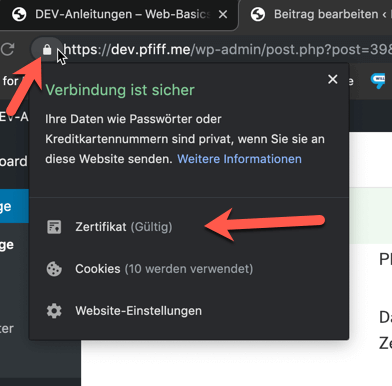
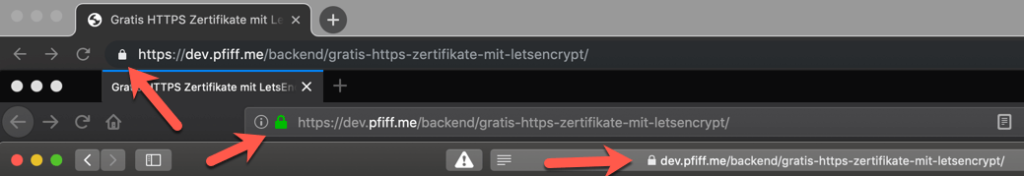
Valid HTTPS certificates are necessary to show the lock beside of your URL.
Types of Certificates
- Self-Signed Certificates
- Everyone can create certificates and implement them in their websites.
- But these will NOT be marked as “secure” and therefore don’t get a lock symbol.
- To use these certificates every client has to mark these certificate as “secure” once in their system..
- Wildcard Certificate
- Are often used for Subdomain Certificates so you don’t have to create a new certificate when you add a new subdomain to your server.
- Example: *.pfiff.me
- Domain Validation (DV)
- Here the applicant is being checked if he is actually the owner of the given domain. No other information like the identity of the company is being checked and therefore no other information is being displayed in the certificate.
- Wildcard-Certificates are possible!
- This is the default approach for LetsEncrypt certificates.
- Organization Validation (OV)
- Basically the same as a DV but additionally the companies name and locations is being checked. These information are then being displayed in the certificate.
- Wildcard-Certificates are possible!
- Extended Validation (EV)
- Same as OV, but it’s a more detailed check of the company.
- In the past with an EV certificate the name of the company was being displayed next to the lock but this feature has been removed from every currently common browser (Chrome, Firefox, Safari etc.). Therefore its debatable if this option is a good choice.
See https://www.troyhunt.com/extended-validation-certificates-are-dead/
- Wildcard-Certificates are NOT possible!
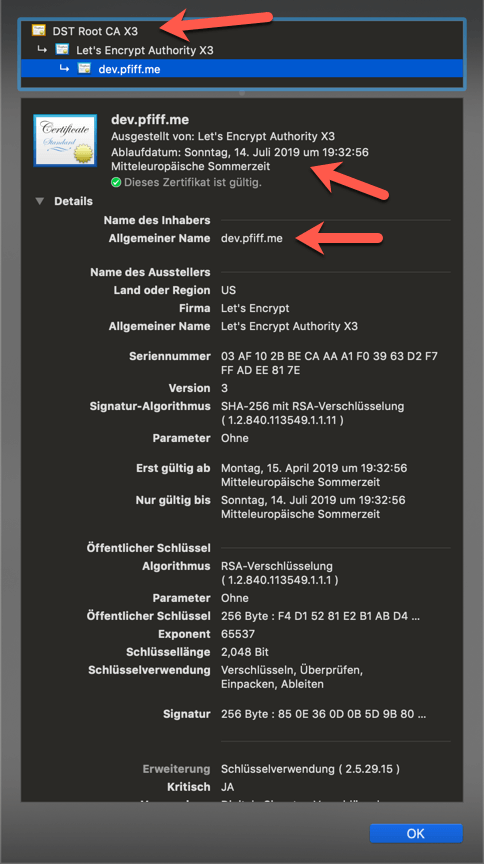
What is a “Certificate Authority” (CA)?
A “Certificate Authority” (short CA) is necessary to check certificates with specific, predefined methods and if that validation has been successful to sign these certificates. Additionally on each validation the certificate a date will be set when the certificate is being expired. After that period the certificate has to be checked and signed again.
In the past it was only possible to buy HTTPS certificates. But since 2015 “LetsEncrypt” or better the python script “Certbot” which makes this process way easier.
LetsEncrypt uses the “Domain-Vaildation” (DV) process. Therefore everyone, who is the owner a domain and shows the domain to a server, a signed LetsEncrypt certificate can be generated for this server to use this domain.
What is Certbot?
Certbot ist a software, which automatically generated and manages HTTPS certificates.
Currently there are even plugins available for the 2 mostly used webservers (Apache and NGINX), which even handle the configuration for the vhost files to include the certificate.
The easiest way to use certbot is to go to https://certbot.eff.org, enter your OS and your uses webserver and follow the instructions.
Usually a certificate generated by Certbot/LetsEncrypt is valid for 90 days. But Certbot checks the status of each installed certificate regularly and automatically renews certificates which will get expired in 30 days.
Therefore you only need to create and install your certificates once and everything else is handled by certbot.
Informations of a certificate